- 4.2Login
- 4.2.1Anonymous user access
- 4.2.2Login providers
- 4.2.2.1Demo
- 4.2.2.2Password (internal provider)
- 4.2.2.3Ldap
- 4.2.2.4Oauth
- 4.2.2.5Preconfigured oauth providers
- 4.2.2.6Configurable oauth providers
4.2Login
The login section provide the configuration space for:
- anonymous user access
- login providers
4.2.1Anonymous user access
Anonymous access allows read-only access to the entire application. Users will be able to navigate projects, boards, and cards without the need to login in.
By default, the access for anonymous user is disabled.
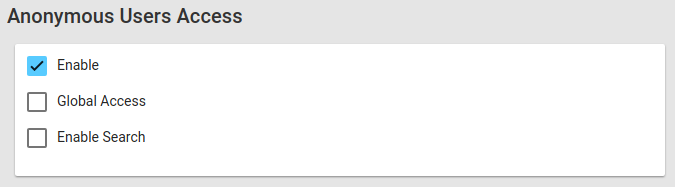
Once enabled, it’s possible to configure further settings:
- Global Access: give access to all project, regardless of each project anonymous access policy
- Enable Search: enable search for anonymous users
If only one of few projects should be accessible without login, enable anonymous access for each one individually.
To do that, access the “Anonymous Access” tab in the Project Settings.
4.2.2Login providers
Lavagna support multiple providers at the same time. In this section they can be enabled and configured.
4.2.2.1Demo
The Demo provider is used for development and internal testing. Users belonging to the demo provider have their password automatically set as their username, without the possibility to change it.
4.2.2.2Password (internal provider)
The internal password provider is used for deployments that have no ability to connect to an external authentication provider, and enforce security via other means (e.g. access via VPN only).
Simply enable the password provider to start using it.
4.2.2.3Ldap
If the users are stored in a ldap directory (Active Directory is supported too), the ldap provider must be configured.
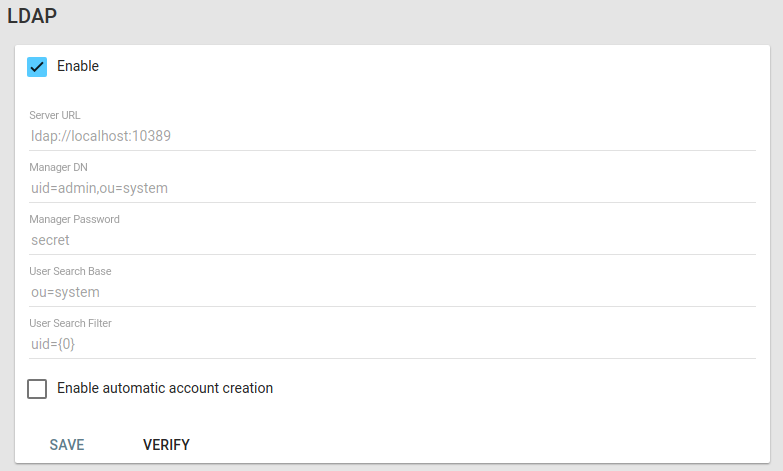
It requires a user that can query the directory (the Manager DN and Manager Password).
The query is composed by a base (Search base) and the filter (User search filter), where {0} is the placeholder for the username.
The configuration can be tested in the “Verify” form.
By checking “Enable automatic account creation”, Lavagna will automatically create missing users, with DEFAULT role, if the LDAP authentication succeeds, but the user is not found internally.
4.2.2.4Oauth
The application support the following external oauth providers:
4.2.2.5Preconfigured oauth providers
Select the oauth provider of the first account and provide the api key and secret. The provided callback url should be the correct one that must be provided.
See the documentation for:
- bitbucket
- gitlab. Registration page is https://gitlab.com/profile/applications
- github. Registration page is https://github.com/settings/applications/new
- google: the “Google+ API” must be enabled
4.2.2.6Configurable oauth providers
Self-hosted gitlab instances can be configured with the “Add new provider” functionality.
Please note that if you are using self signed certificates you must include them in the default keystore of your java virtual machine. See the keytool documentation and this stackoverflow post. Lavagna will not provide a way to ignore untrusted certificates.
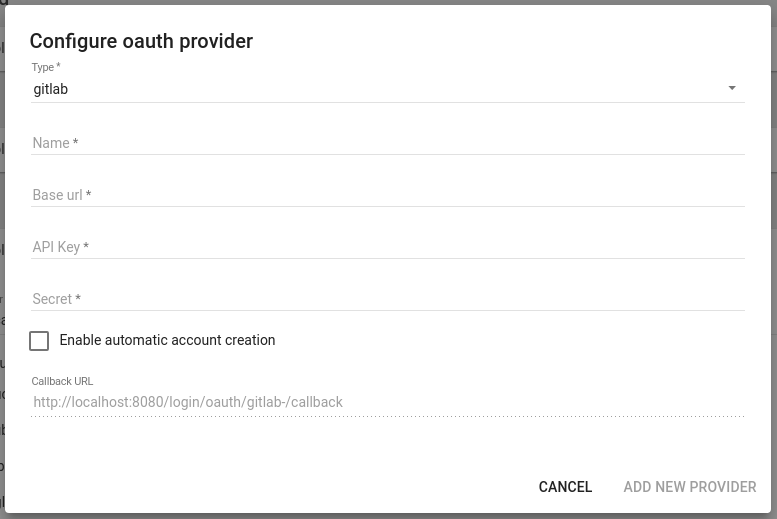
The new providers will appear in the section “Configurable OAuth providers”.